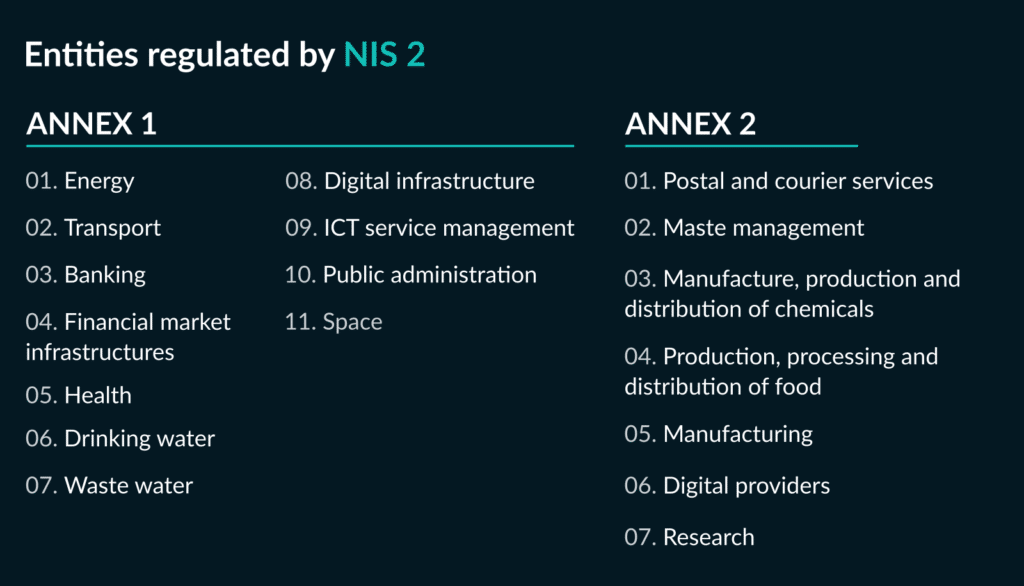
The Network and Information Security 2 (NIS2) Directive will enter into force in 2024. Adopted in November 2022 by the European Parliament, this directive builds on the NIS1 Directive, in force since 2018, which aims to streghten the cybersecurity of major players in 10 strategic sectors.
But the NIS2 goes further in reinforcing and clarifying the obligations set out by its predecessor. Notably, it extends these measures to thousands of other entities – public and private – in relation to how critical their operations are. An opportunity for countries and Europe as a whole to collectively strengthen our guard against cyberattacks that are coming at us harder and faster than ever.
So, how do we get ready for it? What tools and methods can we use?
Is my organization affected?
According to a report by the French National Cybersecurity Agency (ANSSI), more than 60% of reported attacks involve smaller entities: microbusinesses, SMEs, mid-size companies and local authorities. This means that no organization is spared.
In the face of these cyberattacks, we need to strengthen security measures for all companies in Europe we deem important or critical. NIS2 regulates private entities, public administrations and local authorities. In France, this equates to thousands of entities in more than 18 industries.
The applicability criteria have been defined at European level – mainly the number of employees (>50) and/or turnover (>€10 million), as well as the nature of the activity carried out by the entity.
But transposing NIS2 into national law could also include special cases, subjecting entities to this regulation that don’t yet meet the criteria. Examples of entities mentioned are those:
- carrying out activities that may have a significant impact on public safety, security or health;
- carrying out cross-border activities that may have a systemic impact;
- of specific importance at national or regional level.
What are the new obligations under the NIS2?
It is still a little early to publish any document that brings together all the regulatory requirements of NIS2. Member States still have until 17 October 2024 to transpose NIS2 into national law. In the meantime, stakeholders will be consulted to ensure that regulations take account of their situation, as well as the economic and operational costs of the measures.
What we do know, though, is that the security measures provided for in NIS2 will comprehensively cover the policies and procedures of organizations relating to risk analysis, IS security and the use of cryptography. This includes:
- incident management
- business continuity
- supply chain security, including suppliers and contractors
- security of human resources, access control policies and asset management
- cyberhygiene and training staff in cybersecurity
- multi-factor authentication or continuous authentication solutions, the use of secure voice, video and text communication solutions, and secure emergency communication systems within organizations.
What should you do in the meantime?
Until we know the exact obligations you will need to comply with, you can start setting up prevention processes and taking actions to address the security risks.
One thing for you to work on is hardening your systems: this involves putting in a set of measures designed to reduce your system’s exposure to attacks through relatively simple actions, such as removing unused services and limiting rights and access to only the users who need them. Sounds basic, but it works a treat!
─ Afnic
Another thing to implement is patch management, which prevents exposing your machines with out-of-date systems and applications to potential or proven security vulnerabilities.
System hardening and patch management are two essential pillars to securing your systems in depth. These are recommended by major security standards, such as SecNumCloud, ISO 27001 and CIS Benchmarks.
The new obligations imposed by the NIS2 Directive will be in line with these national and international standards. Adopting these common-sense measures is well worth the time: you will get ahead of the legislation and boost your level of protection in one swoop.
Can we automate security?
Compliance and security go hand in hand. With the NIS2 Directive entering into force very soon, these two aspects are even more complementary and inseparable than ever. Compliance means you can ensure and demonstrate security over time.
That is why automated infrastructure tools such as Rudder now include security reinforcement and compliance monitoring features – ideal for automating everything you can, so you get a firmer grip on your system security. From deploying and auditing security configurations and performing vulnerability assessments, to managing patch campaigns and threat remediation.
Why Rudder?
Rudder helps companies secure and control their entire IT infrastructure through automation. Our solution includes all the features you need to boost your system security and demonstrate your compliance with certification or legal requirements such as NIS2. Thanks to its easy-to-use visual interface, Rudder is an ideal tool for you to report any security incidents to your competent authority.
With rigorous traceability of the status and actions carried out on your systems, Rudder allows you demonstrate compliance at all times.
As a member of CIS SecureSuite®, our team can help you evaluate, implement and monitor your company’s cybersecurity policies and guidelines.
More information on NIS2: https://digital-strategy.ec.europa.eu/en/policies/nis2-directive
